The entire purpose of deploying a honeynet is to collect data. However, that data has no value if it cannot be analyzed. Walleye interface is the graphical tool available for analyzing the logged activities and alerts. Walleye also supports the integration and analysis of sebek data. The power of sebek data is that it captures all of the system activity and gives the ability to analyze what happened on the honeypot, even if the attacker went in encrypted.[1]
On opening the management interface in the browser (https://ip-address-management-interface), administrator will be prompted to login. This is a SSL connection. The default user is roo and password is honey. Administrator will then be prompted to change the password. [2]
This section discusses the data captured and analyzed through the walleye interface. Walleye interface facilitates the analysis of data on the basis of source IP, destination IP, source port, destination port. The protocols used for analysis are TCP, UDP, and ICMP. However sebek data is also captured and analyzed.
Attack Profile
In order to test the functionality of honeynet, some simulated attacks are launched. Although this simulation does not actually hack the target machine, but it provides deep insight about the working of honeynet and how walleye displays the data from MySQL database.
As a beginner, the simplest attacks that can be launched are packet fabrication without SYN flag, DOS, smurf attack, flooding by using IP spoofing etc. The tool used to do so is hping3. [3]
The command used to launch the attack is hping3. One of the customized ways to do this is to use the option flood with the command to launch flooding on a target IP. Administrative rights are required to run the mentioned command from the attacker’s machine. The attacker’s machine is placed in the production network. [4]
#hping3 -V -c 1000000 -d 120 -S -w 64 -p 445 -s 445 --flood --rand-source <Victim IP>
Source IP can also be spoofed with –a option in this command. The logged entries against spoofed attacker IP do not depict the actual IP of the attacker. [5]
There are some numeric options that represent UDP/ICMP protocol in the command i.e. flooding is done through which protocol. These options are -1 for ICMP, -2 for UDP protocol. For TCP protocol, different flags can be used as mentioned (S for SYN, R for RST, A for ACK etc.) in the sample command above.
V= verbose ; c= packet-count ; d= data-size ; S= SYN flag ;w= winsize ;p= port; s= base source port
Result
Flooding attack is launched in different scenarios with different protocols. There are three scenarios created to launch the attack and analyze the consequences on walleye interface. the three scenarios are based on TCP, UDP, and ICMP protocols respectively.
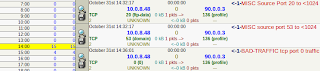
Scenario 1 – Use of TCP SYN flag to flood the target machine (honeypot) The command used for this scenario to launch flood attack on victim machine is:
hping3 -V -c 10000 -d 120 -S -w 64 -p 445 -s 445 --flood --rand-source VICTIM_IP [23]
Figure 1. Flooding the honeypot with TCP traffic
Scenario 2 – Use of UDP protocol to flood the target machine
The command used for this scenario to launch flood attack on victim machine is:
hping3 -V -c 10000 -d 120 -2 -w 64 -p 445 -s 445 --flood --rand-source VICTIM_IP
Figure 2. Flooding the honeypot with UDP traffic
Scenario 3 – Use of ICMP protocol to flood the victim machine with IP spoofing
This scenario uses ICMP protocol to ping the victim machine repeatedly. It is observed that millions of IDS are logged against a single connection within a few minutes of launching the attack as shown in figure 4. The number of packets and bytes transferred from the attacker’s machine are quite large but the incoming packets and bytes in response are 0 because the command is run with two special things:
- IP spoofing used by the attacker to launch the attack (option –a in command).
- Use of broadcast address of the victim machine.
The command used to launch attack using ICMP protocol is:
hping3 -1 --flood -a VICTIM_IP BROADCAST_ADDRESS
Figure 2. Flooding the honeypot with ICMP traffic
References
[1]"International Journal of computer Applications (0975-887)",Gurdip Kaur and Jatinder Singh saini
[2]“Know Your Enemy: Honeywall CDROM Roo”, 3rd Generation Technology, The Honeynet Project.
[3]“Hping”, www.hping.org
[4]Johny, Awad, Andreas, Derdemezis, 2005. “Implementation of a High Interaction Honeynet Testbed for Educational and Research Purposes”, MsITT Thesis, AIT.
[5]Zereneh, William, 2010. “Packet Crafting”.
References
[1]"International Journal of computer Applications (0975-887)",Gurdip Kaur and Jatinder Singh saini
[2]“Know Your Enemy: Honeywall CDROM Roo”, 3rd Generation Technology, The Honeynet Project.
[3]“Hping”, www.hping.org
[4]Johny, Awad, Andreas, Derdemezis, 2005. “Implementation of a High Interaction Honeynet Testbed for Educational and Research Purposes”, MsITT Thesis, AIT.
[5]Zereneh, William, 2010. “Packet Crafting”.